
Ubiquitous Network
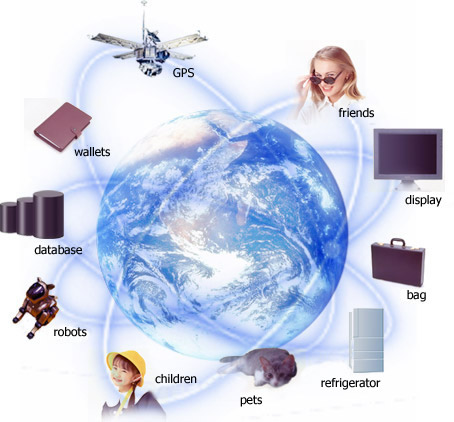
The picture of the Earth shown in the above Chart demonstrates the future situation of the Internet spread throughout the world. It shows everything will be connected to the Internet. We can assume the society in the future where anyone can obtain and dispatch any kind of information at any time from anywhere, whenever you want it. This kind of society is called "ubiquitous society".
Equipment to connect to the Internet is made in very small size and it can be installed in any manner possible. If equipment is small enough, power may be supplied from the solar battery floating in the space by way of micro waves. Network is broad-banded and connected all the time and it can be used freely. If wireless technology is used, location of network connection equipment can be moved freely. The place of dispatch can always be located in conjunction with Global Positioning System (GPS).
In the research at the level of universities, new research themes need to be searched, assuming this kind of society. I want to show you below some examples, which can be realized in the ubiquitous society.
- You can communicate with your aged relatives living far away without worrying about communication fees.
- You can receive information of the health status of an aged person automatically from the sensor attached to him or her.
- Your children or pets will never get lost because you can always locate them.
- You will feel no anxiety about losing money, as your purse is connected to the Internet.
- When you pass by a convenience store, you will get a request from your refrigerator to buy a pack of milk.
- Television will tell you when your favorite program starts. Even if you are out of home, you can reserve a video setting from outdoor.
There will be many more examples, and there may be many more applications which you can not imagine at present. Ubiquitous network is the system to offer people the foundation of network to realize this kind of ubiquitous society.
Network Security
However, if everything is connected by network, such a situation may conversely become a cause of new concern. The situation undoubtedly offers crackers an easy chance to intervene. You certainly want to keep the place of your purse to yourself without letting others know the whereabouts. If someone else has come to know your whereabouts without your permission, it is certainly an infringement of your privacy.
There, we need a system to utilize ubiquitous network in a very safe matter. Here exists the necessity of network security. Without such a technology, we cannot use the Internet at ease. It is necessary to use different kinds of network security, depending on the place and circumstances where the Internet is used. Necessary security levels, amount of operational management load and performance are important indices for evaluation.


