GSCIP
There are various ways to realize FPN. If strict security is required, conventional IPsec technology will be suitable, and for realization of mobile environment, Mobile IP technology may be used. A technology combining the above two is also under study. However, as I stated above, there is no technology developed yet, which is capable of satisfying flexibility required by the environment of FPN. GSCIP is a series of proposals to meet the requirements. GSCIP package (a group of software to realize GSCIP) has been worked out by modifying the kernel of Free BSD, and we have been conducting our research under the policy of making open all of our findings.
Basic Concept of GSCIP
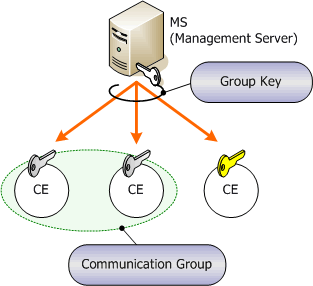
The basic concept of GSCIP is quite simple. Communication entities (CE) having the same encryption key form a communication group (Fig.10). This encryption key is called "group key". CEs of the same communication group communicate each other in cipher by using their group key. GSCIP can flexibly deal with different situations, whether CEs are by sub-network units, by individual units, or by a mixture of both. The group key is periodically renewed by management server (MS).
Components of GSCIP
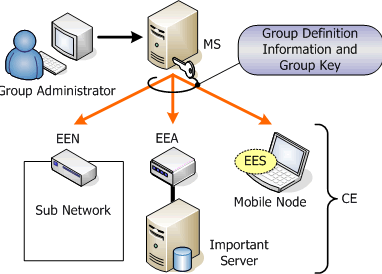
It is the EE (Encryption Element) which actually forms a communication group among CEs (Fig.11). There are several types of EEs, such as router-type EEN (Encryption Element for Network) which has a sub-network under itself, bridge-type EEA (Encryption Element for Adapter) which has a server under itself, and software-type EES (Encryption Element for Software) which is installed in a mobile terminal. MS only defines communication groups and does not manage the relation of EE’s physical location. MS, after strict checking of authentication, provides each EE with the group definition information and a corresponding group key. For the purpose of authentication between MS and EE, the mechanism of PKI (Public Key Infrastructure) can be used. In order to maintain good security, group keys are renewed periodically.
Action Mode
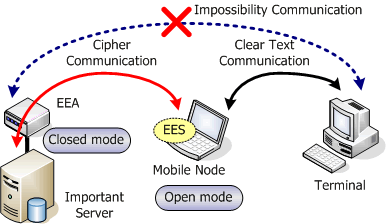
As EEs, there are two kinds of modes; namely, one is "Closed mode" which prohibits communication with non-group members, and the other is "Open mode" which allows normal communication (Fig.12). Closed-mode EE is used to prevent any illegal intrusion and located at the entry of a sub-network or just before an important server. On the other hand, open-mode EE is applicable to client users in general and allows access to common servers. Open-mode EE is also applied to proxy servers which enable users within a sub-network in the closed-mode EE to communicate with outside users.
Unit of group members
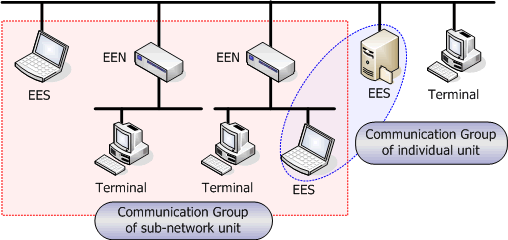
As group member units, there are two kinds of units. One is "individual unit" (for each right holder) and the other is "sub-network unit" (for each sub-network) (Fig.13). The individual unit allows a very fine definition and can be realized by EEA or EES, while the sub-network unit can lessen management burden as the management unit is large and is realizable by EEN. EEA, EES and EEN can coexist. Taking the example of companies, while communication groups of some divisions are constructed with EENs, there may be cases where a specific member of the division participates in an inter-office horizontal project holding EES, that is to say, the member belongs to a different communication group. Communication grouping can correspond to the grouping of people undertaking the same kind of work.